Introduction to Single Sign-On
A Brief History

Eventually, Apple’s iOS and Google’s Android OS superseded Windows. The popularity of these new operating systems in the consumer market proved deadly for Windows’ tenure in the enterprise environment.
That year, Android OS took the lead when Motorola (now Zebra Technologies) introduced the MC40, and Honeywell launched the Dolphin Black devices. These were the first enterprise-rugged devices on the market with the Android operating system. Learn more about Access Made Easy: Embracing the Magic of Frictionless SSO
Nearly a decade later, Android has become the standard for rugged company-owned mobile devices.
Android in the Enterprise
Visit any of the largest retailers in the world, and you will likely spot an employee stocking, price checking, or performing “buy-online pick up in store” (BOPIS) activities with a rugged Android mobile device. These devices offer a wide range of features that allow end-users to access the tools they need.
The increased capabilities of these devices help companies improve visibility into business-critical data to drive their business strategy. At the same time, devices also empower employees as they perform their daily activities and support customers. However, with increased connectivity to workplace systems, and applications, these devices have become targets for hackers and malicious users.
Since these devices can reach company data and workplace networks, hackers have begun to use them as entry points for malicious activity. Robust security management is a requirement for device and workplace safety. Protecting customer, employee, and company data should always be at the forefront of a security plan.
This guide will do an in-depth breakdown of single sign-on (SSO) and all its components. This guide is essential for understanding the importance of Android Authentication, security, and shared device usage. Foundational knowledge of how SSO can benefit an organization is critical to success. This guide is relevant to organizations with devices operating in shared scenarios.
Streamline your authentication process with SSO – Contact Bluefletch for guidance!
This guide is for IT professionals looking for guidance on reducing the risk exposure of enterprise Android devices.
If your company’s mobility landscape meets the following criteria, this guide may apply to you:
- Company-owned Android Devices
Most companies purchase devices for their employees to use. Other companies (typically in contact scenarios) will require workers to provide their own devices. This paper focuses primarily on company-owned devices in shared systems. - Shared Devices Amongst Users
In many organizations, devices operate in shared scenarios where workers from different shifts will leverage the same devices. Common shift work scenarios include retail, warehouse, manufacturing, hospitality, healthcare, and transportation workers. - Ruggedized Android or Dedicated Consumer Android Devices
Ruggedized Android devices are the most prominent choice in shared enterprise environments. Some companies use consumer devices with rugged cases, but Android is most common for dedicated shared roles.
If you are responsible for the following:
- Deploying and Supporting Mobility – Organizations typically have teams supporting device and software deployment. These teams may fall under infrastructure or IT operations support.
- Developing Applications – Many enterprises leverage internal development teams to build bespoke mobile applications. These apps are designed specifically for their business landscape.
- Securing or Setting Security Policies for Mobile Devices – As mobile devices become more capable, CISO and security teams invest more time in ensuring they are adequately secured.
Mobile technology provides limitless opportunities across the enterprise. Unfortunately, all of the potential areas for opportunity can not fit in this guide. Before moving forward, here is a list of things this guide will not cover.
This guide does not cover any of the following aspects of the enterprise mobility landscape:
- Apple iOS Devices – Apple iOS devices are popular amongst consumers for their cutting-edge hardware, consistent simplistic user experience, and focus on user privacy. Unfortunately, for more complex enterprise use cases, Apple’s consumer focus makes devices challenging to use in shared device scenarios.
- Windows Mobile or IoT Devices – After the death of Windows Mobile/CE, Microsoft cut its investment in the mobile landscape. They have recently begun introducing Windows Surface tablets and IoT devices.
- BYOD Devices – May companies let employees use their personal devices to perform work activities. These use-case scenarios are known as “Bring Your Own Devices.”
- Individually Assigned Devices (Personal carry devices) – Individually assigned devices are similar to BYOD devices but are only for a single user. Examples of such users are company executives, pilots, flight attendants, doctors, store managers, and more.
BlueFletch began evaluating the use of Android devices in the enterprise over a decade ago. At the time, Android technology was very new, and most companies were concerned that Android had too many security risks to be leveraged in the enterprise.
These concerns were typically driven by the following:
- A lack of understanding of Android security practices.
- The availability of cheap Android devices leveraging non-Google app stores fraught with malware.
- A lack of good tooling to secure Android devices.
In 2011 we built a set of tools focusing on Android login and lockdown. These tools were used for several years as we helped large enterprises migrate apps and deploy Android devices in shared end-user scenarios. In 2018 we made our Android Enterprise Launcher (with supporting tools) a stand-alone offering that companies could license.
This guide summarizes best practices for single sign-on, authentication, and access control that our team has learned over the last decade. As with any guide, our guidance may not apply to everyone.
Fundamentals of Authentication and Single Sign-on
What is Authentication?
Authentication is the process of verifying the identity of an entity (end-user), device or system. Within the enterprise, authentication is an important security measure that helps ensure only authorized users can access sensitive data and workplace systems.
There are many different ways to authenticate the identity of a user, and the appropriate method will depend on the specific needs and requirements of the organization. Some standard methods of authentication include:
- Password-based authentication is the most common form of authentication and requires users to enter a unique password and username to access company-owned devices.
- Biometric authentication uses physical characteristics, such as a fingerprint or facial recognition, to verify the identity of a user.
- Token-based authentication uses a physical object like a security token, FIDO key, or smart card to authenticate the identity of a user.
- Two-factor authentication requires two types of authentication to access a system or device, such as a password and a randomly generated pin code.
In the context of shared workforce mobile devices, it is essential to implement robust authentication measures to ensure that only authorized individuals can access sensitive information and systems. This can help to prevent unauthorized access and protect against potential security breaches.
Enhance security with expert SSO solutions – Schedule a call with our team!
How Authentication Works
Authentication is broken into a few distinct parts. First, an entity provides information that proves its identity, such as a password. Next, the system or device being accessed will cross reference this information with the data on file for the given user. If an entity’s provided password matches the password stored for that user, access is granted.
Proof of identity is related to one of three things:
- Something they know includes a password, PIN, or codeword that they use for their workplace systems and devices. These are typically the first layer of security in the enterprise and are commonplace for standard authentication procedures.
- Something an entity has is a key, token, NFC badge, or email account access. These elements are usually associated with a user’s account or device.
- Finally, something a user is relates to biometric features. Examples include fingerprints, faces, and retinas. Biometric technology, such as fingerprint scanning and facial recognition, captures said parts
Authorization and How It's Different from Authentication
Authorization validates that an entity has access to a requested resource. Authorization policies are rules that determine levels of access based on given attributes like roles, groups, or individually set permissions. Authorization relies on authentication to prove the identity of an entity.
Authorization is a critical component of enterprise workplaces with a wide variety of on-site applications and systems. For example, in a shared device retail scenario, a back-end warehouse employee does not need access to the same applications as a front-end floor employee.
With advanced authorization tools, an organization can delegate access on an individual level to ensure that each employee only has access to appropriate applications for their role. This way, when an employee picks up a shared device and successfully authenticates their identity, the system can automatically authorize the request to grant access to their assigned applications.
What is SSO (Single Sign-On)?
Single sign-on (SSO) is a feature that allows users to log in to multiple applications with a single set of credentials. This can be particularly useful for organizations with various applications that their employees or customers need to access, as it eliminates the need for users to remember multiple sets of credentials.
Additionally, SSO solutions enables organizations to manage resource and application access across their network. Organizations can delegate individual users and role-based groups access to specific applications. This level of customization helps create a controlled shared environment for organizations and IT admins to oversee shared device security.
Single sign-on can be implemented on Android devices using various technologies, such as OAuth or SAML. These technologies allow users to authenticate their identity with a central identity provider, such as Google or Microsoft, and then use that authenticated identity to access multiple applications without entering their login information again.
Users typically need to install a compatible application or browser that supports the chosen SSO technology to use single sign-on on an Android device. Once the application is installed, users can log in to their account and be granted access to the other applications they want to use. From then on, they can access those applications simply by opening them on their device without entering their login information again.
Users can access their entire library of approved workplace applications with one successful login. Secure sessions ensure that users can alternate between applications for the duration of their shift without additional authentication.
Single sign-on eliminates needing to remember and re-enter multiple, unique credentials throughout the workday. This drastically decreases the need for password reset and password fatigue.
Single sign-on can improve user experience by reducing the number of times users need to enter their login information. It can also enhance security by eliminating the need to store multiple login credentials on individual devices.
A Seamless Login Experience
Passwords are essential to keeping shared devices secured, but entering passwords for multiple apps throughout a work shift can be time-consuming. Depending on a company’s password requirements, the login process can take between 30 and 90 seconds. During this time, employee frustration levels rise while productivity drops.
With single sign-on, one successful login replaces every handful of login attempts. Not only is this a stress reliever for users with password fatigue, but it’s also a tremendous time saver. We’ve found that users take an average of 42.3 seconds to log into shared devices with a traditional password. Single sign-on reduces login time to an average of 2-3 seconds by streamlining the number of times a user has to enter their credentials.
Without single sign-on, those 42.3 seconds add to a yearly loss of hundreds of thousands of dollars in additional support costs and decreased productivity. We’ve found that companies implementing SSO with BlueFletch Enterprise save upwards of $871 per year per device. Over the years, these savings can accumulate as more device fleets adopt SSO as their standard login security protocol.
On top of this, our fast re-authentication is compatible with technology such as facial recognition, NFC badge taps, Multi-Factor Authentication (MFA), and FIDO2 keys. These alternative methods of authentication provide their own set of benefits that are explored further later in this guide.
Reducing Password Fatigue with Single Sign-on
Tech.co writes that the average person has around 100 passwords across all internet accounts and services. This number is only a median, and with more of our daily lives moving online, this number will likely increase over time. Try to think of all the things in your life that you have 100 of. Friends, books, records? Maybe you’re into fashion and have 100 pairs of shoes. Could you name all of them? Chances are no; you can’t, so how are expected to juggle so many unique passwords?
The likelihood that anyone could remember all 100 passwords off the top of their head is low. And it’s even less likely that every single one of these passwords is unique and robust. NordPass, a proprietary password manager, put together a list of the most popular passwords of 2019.
This article aimed to shed light on the importance of passwords by highlighting the millions of people who “pick 12345 as their password.” They found that a significant number of people still use unsecure passwords, leaving their bank information, addresses, and personal records vulnerable to attack. This is alarming when paired with the millions of individuals falling victim to cyberattacks yearly.
Placing this research inside the enterprise context brings some severe issues. If lazy passwords are shared outside the workplace, these same individuals will likely get their bad habits to work. However, when shared devices are left vulnerable, it’s not only the individual’s information that’s at risk. With access to secure company systems, a hacker could expose sensitive data related to other employees and clients.
The root of the issue is that most people want a password that is easy to remember. No one wants to spend the first few hours on a Monday morning entering passwords or waiting around for a reset. Poor password management opens holes in company security in a dynamic environment where an end user has access to multiple accounts and applications. Users frustrated with forgotten passwords and failed login attempts are more likely to experience password fatigue.
Password fatigue creates a domino effect across the enterprise. One overwhelmed employee may forget their password(s) and then wait for a password reset while clogging up the helpdesk ticket queue. In the long run, this cycle costs an organization thousands in support costs. However, it’s not the employee’s fault. The weight of password fatigue starts at the root, the organization’s password management system.
With SSO, employees come to work focused and prepared for a productive day, knowing they can pick up a shared Android device and access every application with one set of credentials. No more stressful Monday mornings if you are trying to remember your password. No more weekly calls to the helpdesk about that one account you keep losing the password for. Single sign-on ensures that both the end-user and the organization feel equipped to take on the workday.
Reducing Helpdesk Tickets with SSO
The more accounts, applications, and networks employees require, the more passwords they’ll have. All of these passwords are crucial to maintaining the security posture of an organization’s network. Therefore, regular mandatory password resets and password character requirements are standard for most workplaces. However, the need for more complex passwords increases the number of forgotten or misplaced ones.
Users may call and need a password reset for a myriad of reasons. Including but not limited to:
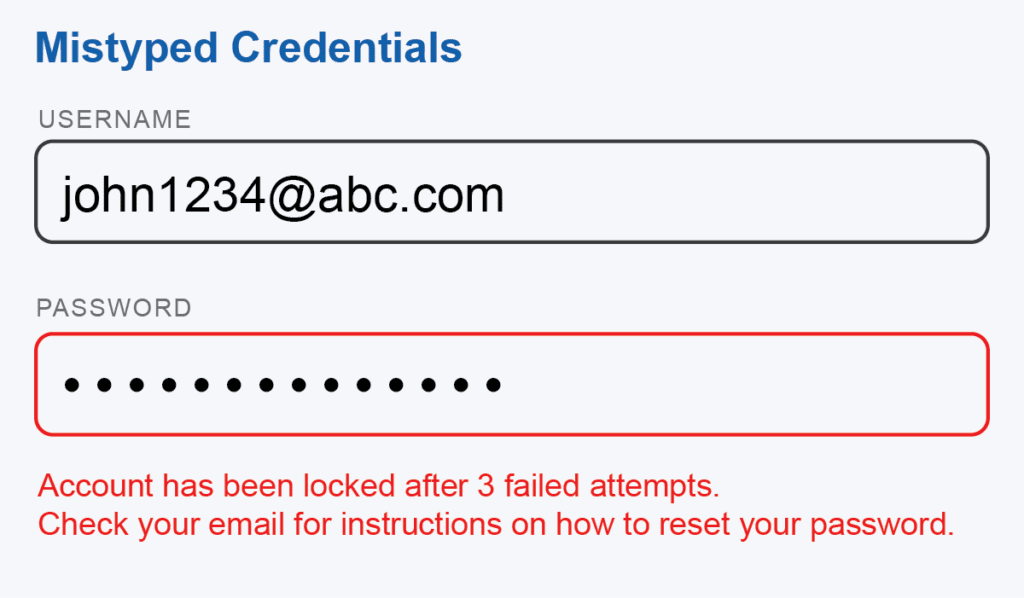
Android Mobile Device screens are small, and mistyping characters is easy. Especially when warehouse or field employees are wearing gloves, which makes interacting with a touchscreen rugged, this little mistake often concludes with locked accounts and various calls to the help desk.
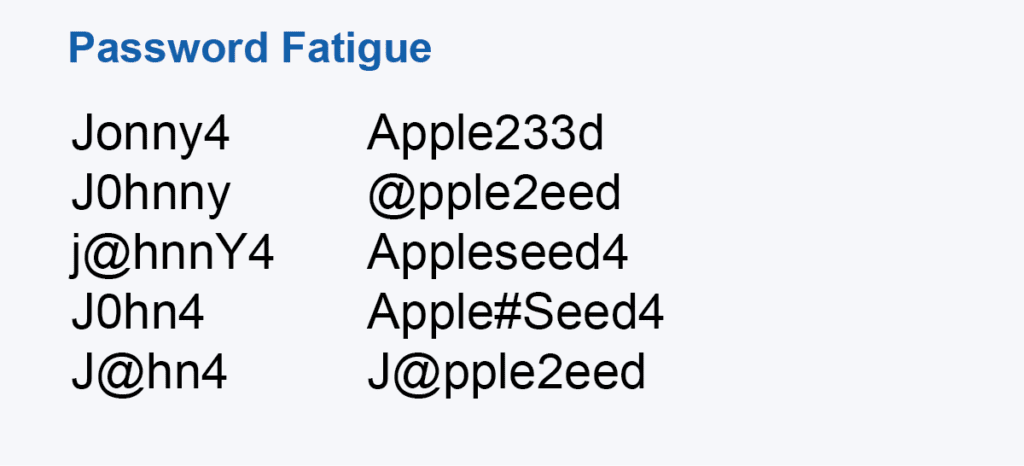
Having an extensive collection of workplace passwords comes with a mountain of pressure. Many employees fear the day they forget the password to a critical account. Data has shown that having an overwhelming number of passwords to remember contributes to lost and forgotten passwords. Limit the number of passwords required to one, and drive down password fatigue.
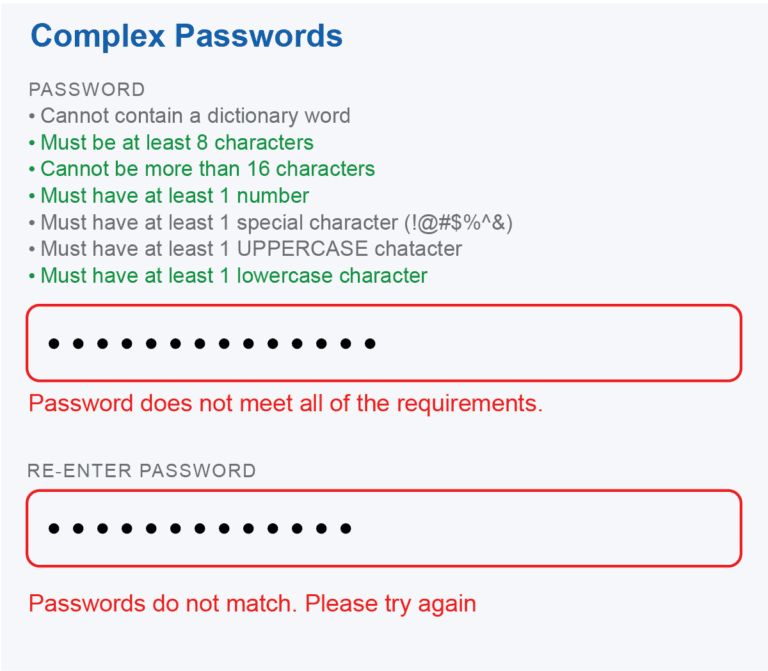
Password resets may be a simple task for a helpdesk team, but reset tickets become a considerable expense when multiplied by the hundreds of employees and account across an organization. Helpdesk professionals are an essential part of an organization’s day-to-day. They help keep your end-users productive with the tools and assistance they require. They’re equally critical for maintaining an enterprise’s security upkeep, monitoring for breaches, and protecting company networks.
So help keep IT professionals productive by reducing the time dedicated to password resets.
The Danger of Data Breaches
Recently, Kommando Tech estimated that “81% of data breaches are due to poor password security” Additionally, “52% of data breaches resulted from malicious attacks, with each breach costing $3.86 million.”
This data is staggering, especially when contextualized within enterprise security.
Statista found that “During the third quarter of 2022, internet users worldwide saw approximately 15 million data breaches, up by 167 percent compared to the previous quarter.” Some organizations have thousands of devices in the hands of their workforce, and with data breaches reaching an all-time high, it’s more important than ever to secure password best practices.
Passwords are one of the most critical barriers to protecting an organization’s data from hackers. Many applications used by retailers contain sensitive company-specific data such as pricing details, ordering details, or customer details. And within a company’s data banks are employee records, financial information, and other sensitive documents that could be damaging if left in the wrong hands. This data requires secure applications and associated accounts to ensure that hackers or nefarious actors can not breach company systems.
How SSO Protects Data
- Protecting Passwords – SSO reduces the risk of unauthorized access to sensitive systems and data by allowing users to access multiple applications with a single set of credentials. This is because it eliminates the need for users to remember numerous login details, which can be lost, stolen, or shared with others. Single sign-on helps prevent unauthorized access to sensitive systems and data, as only authenticated users can access workplace applications and resources.
- Complex Passwords – Companies should implement complex password requirements across the enterprise to maintain security integrity. Many data scientists agree that meeting basic needs like using special characters and a mix of letters is good. ScienceDirect writes, “Complex passwords should contain a good mixture of upper/lower case letters, numbers, and symbols. Passwords should also not be based on dictionary words and should contain at least seven characters (the longer, the better).”
- Alternative Authentication – SSO improves security by using robust authentication methods, such as biometric or two-factor authentication, to verify the identity of users. This prevents unauthorized access by requiring users to provide additional proof of their identity before accessing sensitive systems and data.
- Shared Device Management and Control – Single sign-on centralizes the authentication process and provides a single control point for managing access to sensitive systems and data. Organizations can delegate access roles through SSO and recover device analytics and login data. This makes it easier for organizations to monitor and control access to their systems and data and promptly detect and respond to potential security breaches.
- Session-Based Access – Once single sign-on authenticates a user, they’re part of an authorized, active session while they use the device. Upon logging out, this session expires and entirely cuts off access to the device. If a device is returned to its cradle, left outside the network, or inactive for a set amount of time, the session will automatically expire. The device is unusable when outside of an active session. Applications, data, settings, and all other device features are inaccessible. With single sign-on, organizations can rest easy knowing bad actors and other threats have little chance of obtaining sensitive data without an authorized account.
- Device Accountability – Single sign-on helps maintain device accountability as login and log-out data is tracked and stored. These metrics help paint a picture of who last used the device, where it’s located, and what applications were accessed. When end-users know their activity is being tracked on a shared company device, they’re less likely to lose or steal a device.
Single Sign-on in Retail
Retail organizations that utilize company-owned mobile devices know that end-user productivity drives success. When employees feel empowered by their devices’ tools, the workday runs like a well-oiled machine. SSO is effective in shared device environments like the retail space where multiple applications are required. Single sign-on provides end-users easy access to inventory management and customer care tools most efficiently, as users can access all their approved applications within seconds.
Physical retail stores are home to a range of different departments and roles. With single sign-on, company-owned devices do not need to be assigned to specific departments. Using SSO’s permission management functionalities, an organization can delegate a subset of applications and resources to be available to particular departments and roles. This allows devices to rotate between employees and departments, as each employee can only access their assigned applications. Upon login, users will find the same set of apps, even if it’s a different device.
When an employee is assigned a role within the system, they will have immediate access to all pre-selected applications upon authentication into a device. This is particularly useful for instruments that rotate between users, as devices can go from the warehouse to the front without any issues. Additionally, pre-approving applications simplify the rollout of new devices and the authentication of new employees.
These customizable application management features enhance the shared device experience for all users. When any company-owned device can cater to the needs of an individual employee, regardless of their role, then the devices are truly “shared.”
Single Sign-On Case Study
We ran a case study with one of our clients to find some metrics around the benefits of single sign-on for shared Android devices with the BlueFletch Launcher.
The following results are based on one of our retail customers who rolled out thousands of devices across its stores.
The company used for this case study was on the conservative end of savings we have seen our customers achieve with an effective single sign-on strategy. Our customers with more SSO-enabled applications and who use devices for more shifts achieve more significant cost savings than what we cover below.
The retailer had an existing Identify Provider (IDP) that human resources provisioned users with when upon being hired. The most common IDPs we see our customers deploy include Okta for android, Azure AD, Sailpoint, and Ping Identity. The BlueFletch launcher has out-of-the-box support for all major IDPs, so there are minimal setup and configuration costs.
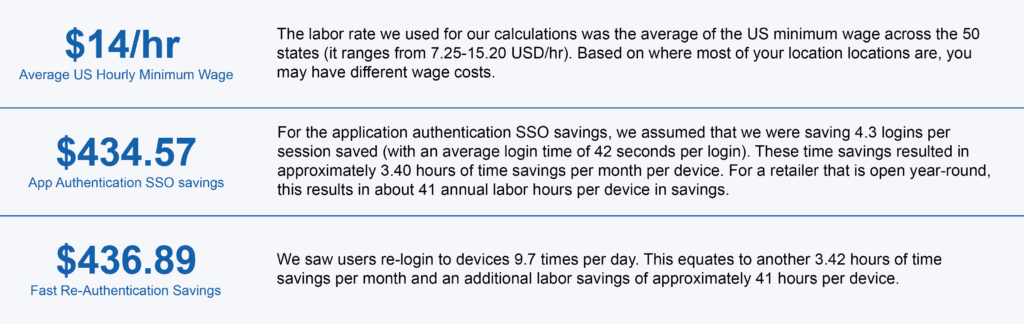
For this analysis, we have normalized the results to an “annual savings per device.”
Data Points:
- 42.3 Seconds per login – Average login time – We define login time as when a user enters their credentials to the point where they can start using the device. Most of the time for login is spent when the user is typing in their username and password. The time for the BlueFletch Launcher to perform the credential validation against the IDP is typically 2-3 seconds of the total login time. For this case study, the retailer used a required password complexity of 12 characters with one uppercase and one symbol.
- 1.8 Shift per day – Sessions per device – The devices for this case study were used on average for 1.8 shifts per day. Based on the operating hours for this retailer, that was consistent with what we were expecting for a fully utilized device.
- 5.3 App launches per session – The average number of applications used per session – We define an application session as a user opening an application that generally requires authentication. We subtract one of the logins from this number to calculate cost savings because users must log in at least once per shift.
- 9.7 Re-authentications per device – Fast re-authentications per day – The BlueFletch Launcher supports fast re-authentications (you do not want unlocked devices to be accidentally left sitting around). This is helpful when a device has timed out and locked due to inactivity. The BlueFletch launcher allows users to tap an NFC badge, enter a PIN, or use facial reauthentication to get back into their session quickly. Fast re-authentication saves users time when logging back into their session following a break or a device timeout when serving a customer.
We concluded that the annual cost savings with SSO and the BlueFletch Launcher would be $871 per device (per year). To calculate this number, we combined the time reduction from application sign-on and added it to the time saved from users having to reauthenticate after time away from their device during a shift.
The following are the contributing factors to this saving:
The Elements of Single Sign-on
Identity Provider
There are many popular IdP options available on the market today. Some significant players include Azure AD, Ping Identity, Okta, OneLogin, and Sailpoint. We will explore these IdPs in further detail in section 3 of this guide.
Controlling Access with an IdP
IdPs are a barrier of defense between protected resources and end-user. IdPs prompt users to authenticate and confirm their identity when accessing a restricted resource. When a verified user enters valid login credentials, the IdP communicates with the respective system to grant access to the resource, application, or design.
User and password management is centralized within an Identity provider. This relieves some of the pressure placed on individual applications to provide sufficient security, as an organization controls all of its applications directly from its IdP. Additionally, when functioning alongside single sign-on, a company does not have to worry about the strength of every individual password an end-user has across all their workplace applications.
Managing these essential security functions within an IdP is much simpler. Removing employee permissions after they exit an organization is simple as well. Since all their accounts are managed inside the IdP, it takes less effort to terminate their access. No need to delete a user’s account within every individual application. In one step, a user can be completely wiped from a given system, protecting an organization.
Usernames and passwords have traditionally been used for authentication across workplace systems. However, many IdPs support multi-factor authentication with tokens, biometrics, text prompts, and secret questions. Additionally, some IDPs support password-less authentication, such as token-based authentication. Using a ticket and a PIN (or another factor) to reduce the number of passwords users must remember.
Grant Permissions with an IdP
Role-Based Access Control allows companies to customize access to resources, services, and applications within an IDP. Place users into roles with access to specific applications and resources only available to the assigned role. These resources may include secure databases, networks, and applications.
Once entered into the system, users will have access to every resource assigned to their designated role. Upon login to a shared device, the IdP identifies the user’s roles and provides access. An organization can also re-assign users into new parts if an employee switches roles or job responsibilities within the company—Role-Based Access Control streamlines permission management by centralizing resources into groups.
Identity and Access Management (IAM)
Identity and Access Management (IAM) is the term used to describe the policies, processes, and systems enterprises use to manage users and control what resources users are allowed to access. For enterprises, IAM systems are typically the foundation of their cybersecurity strategy.
The typical elements of an IAM framework include the following:
- User Provisioning
- Identity Management – IDP, Directory, Federation of Authentication
- Authorization – Resource Access Control
- Auditing Mechanisms
Identify is defined as a set of attributes that device an entity.
Identity Federation
Identity Federation is the relationship between one system (a service provider or SP) and another (An identity provider) to provide information about what permissions and rights it may grant a user. Establishing trust between the two systems must occur before users request system access.
Identify Federation works within many websites that ask users if they want to use their personal Google or Facebook accounts to access a site. Those sites do not get access to your user credentials or account information; they get a response from Google or Facebook that you are an authorized user. As an end user, this benefits you because it reduces the number of sites you need to create accounts.
This exchange of information between the two systems happens in the form of a Token. An IdP will exchange a token with a user’s right to grant access to the service provider system. The SP does not hold any user data and will never have access to the users’ login credentials. Tokens help prevent vulnerabilities during the exchange by keeping user data secure.
Tokens
Tokens are digital (sometimes physical) security authentication devices. Systems exchange tokens to confirm and prove a user’s identity. This process is most common within workplace systems and applications, especially in organizations with secure company networks. Tokens keep users’ data safe by encrypting their login information so that an SP does not hold or remember user data.
TechTarget writes that a token “generates a random number, encrypts it and sends it to a server with user authentication information. The server then sends back an encrypted response that can only be decrypted by the device.” This process provides a secure authentication that maintains system security.
SAML
Security Assertion Markup Language 2.0 (SAML) is an open federation standard that allows an identity provider (IdP) to authenticate users and pass identity and security information about them to a service provider (SP), typically an application or service. With SAML, you can enable a single sign-on experience for your users across many SAML-enabled applications and services.
Users authenticate with the IdP once using a single set of credentials and then get access to multiple applications and services without additional sign-ins. Because SAML-enabled applications delegate authentication to an IdP, the SP can automatically grant, revoke, or change the scope of a user’s access to applications and services when an administrator adds, removes, or modifies the user’s information in the IdP.
AWS provides distinct SAML solutions for authenticating your employees, contractors, and partners (workforce) to AWS accounts and business applications and for adding SAML support to your customer-facing web and mobile applications. To learn more, visit Identity federation in AWS.
oAuth2
Open Standard Authorization (OAuth) is the exchange of tokens to validate a user’s credentials for access to an application. With OAuth, applications secure designated access without sharing password data. OAuth also ensures user data doesn’t remain on shared devices. OAuth is an access-granting protocol and delegated authorization system.
OIDC
OIDC is a layer that was created on top of OAuth 2.0 to create a more robust framework around authentication (since OAuth was designed to focus on Authorization). OpenID Connect adds an Identity Token on top of the Authorization tokens you can get from OAuth.
OIDC “allows Clients to verify the identity of the End-User based on the authentication performed by an Authorization Server” while gathering basic “profile information about the end-user.”
OAuth 2.0 is designed for authorization, OIDC is an open authentication protocol layer.
Password Managers
Password managers are vaults that securely store collections of passwords. Password managers can store passwords from a variety of different accounts across all types of applications and websites. Users can add, remove, edit and further manage all their passwords.
This software has risen in popularity within workplaces that require users to carry multiple passwords. It’s becoming increasingly influential for enterprise workforce users to store credentials within a password manager for security and efficiency.
Examples
Popular password managers include
- LastPass
- Dashlane
- LogMeOnce
- Bitwarden
- RememBear
- 1Password
- Keeper
Password managers offer a variety of benefits outside of simply storing credentials. Here are a few examples of how this software aids shared device users.
- Store Passwords
- Remembering passwords can be frustrating and an unwanted source of stress for end-users. Password managers make it easy to keep complex, secure passwords while eliminating the need to memorize them. The only password you’ll need is the master password to access your password manager.
- Autofill
- Some password managers, such as LastPass, have an autofill feature that automatically enters your credentials. When opening an application or website with which you have registered an account, the password manager will paste your credentials for an average of around 42 seconds on device login. Password managers help reduce this login time with autofill.
- Generate unique complex passwords
- Most organizations require end-users to generate long, complex passwords with special characters. These passwords can get up to 25 characters long and are not always easy to remember, especially when you have to change that password every three months. Password managers have a feature that generates complex passwords for you and automatically stores them if you choose to use them. This feature is optional; if you create your password instead, you can deny the suggested password.
Password managers help protect and maintain password security at an individual and enterprise level. They reinforce password requirements and vault existing credentials to keep shared devices safe.
SSO Identity Providers
There is an abundance of IdPs on the market. Here are a few of the most popular providers for retailers:
Azure Active Directory – Azure AD is based on Microsoft’s on-premise directory service Active Directory (AD). Microsoft initially released AD in the early 90s to help companies manage users’ identities on computer networks that leveraged Windows desktops.
Microsoft has taken many successful products over the last 30 years and migrated them to its cloud platform Azure. Azure AD is an excellent example of this strategy. Due to the prevalence of companies that leverage Microsoft’s Office 365 tools, it is easy for companies to purchase or add Azure AD licenses.
Okta – Okta is a cloud-based Identity provider founded in 2009 and focuses on Identity as a service (IDaaS). Since 2014, Okta’s risen as a significant player in fortune 500 companies. Companies are migrating to web-based cloud platforms, and Okta’s position on identity federation fuels its popularity.
Ping Identity – Ping Identity, founded in 2002, is an older company than Okta. But Ping also embraces a cloud-forward approach to helping companies manage identities and federations in the cloud. Ping claims usage in over 50% of Fortune 100 companies.
OneLogin – Founded the same year as Okta, OneLogin has not seen the same market traction as Okta. To grow its cloud IDaaS market share, One Identity/Quest acquired OneLogin.
SailPoint – An identity security platform founded in 2005, SailPoint integrates AI and machine learning technology to provide a cloud platform to help enterprises “see and understand all your identities and their access at speed and scale, delivering the insights that help you stay ahead.”
LDAP – Lightweight Directory Access Protocol is a “standards-based protocol” for directory server interactions. It’s useful for authentication and data storage and retrieval for “information about users, groups, and applications.” LDAP’s data bank capabilities store information from across a network of enterprise applications.
Implementing SSO on Enterprise Android Devices
Single sign-on begins with assessing an organization’s identity and access management (IAM) roadmap. Every organization has a different set of mobility needs, and companies must ensure SSO will provide sufficient support to existing practices. Pre-determining the requirements for single sign-on keeps an organization on track toward its goals.
Next, a company must be prepared to support the software to maintain high output quality. Security is the fulcrum of an SSO solution, and it takes a dedicated effort to keep devices, users, and data safe.
Single Sign-on for OIDC
OpenID Connect (OIDC) is a protocol that allows a user to authenticate with a single identity provider (IdP) and gain access to multiple services or applications. OIDC is built on top of the OAuth 2.0 protocol, which is used for authorization.
When a user wants to access an application, the application sends the user to an IdP for authentication. If their credentials are valid, the IdP sends an ID token and an access token back to the application. The ID token contains information about the user’s identity, and the access token can access the user’s resources.
Because the user only had to authenticate once, they don’t have to re-enter their credentials whenever they want to access a different service or application. This is known as SSO, and the user can access multiple applications and services with the same credentials.
OIDC enables SSO by allowing the user to authenticate with a single identity provider and then access multiple web pages or applications using the same credentials; it also provides a secure way for the app to verify the user’s identity.
SSO for Legacy Applications
Implementing Single Sign-On onto legacy applications can be challenging, but organizations can take a few approaches to achieve this.
One approach is to use a legacy application bridge or proxy. This involves installing a bridge or proxy between the legacy application and the SSO system. The bridge or proxy intercepts authentication requests and forwards them to the SSO system, which then authenticates the user and sends an assertion or token back to the bridge or proxy. The token then returns to the legacy application for authentication.
Another approach is to use an identity federation solution. This involves configuring the legacy application to trust the SSO system as an IdP and configuring the system to trust the legacy application as a service provider. Once this is done, the user can authenticate with the SSO system and access the legacy application without re-entering their credentials.
A third approach is to use a reverse proxy. This involves installing a reverse proxy before the legacy application and configuring it to perform SSO. The reverse proxy intercepts authentication requests and forwards them to the SSO system, which then authenticates the user and sends an assertion or token back to the reverse proxy. Once again, the assertion or token goes back to the legacy application for authentication.
Organizations can also use an Identity as a Service (IDaaS) to enable SSO on legacy applications. IDaaS is a cloud-based service that provides an SSO solution that can be integrated with both cloud and on-premise applications with either SAML or OpenID Connect. IDaaS providers can offer various SSO options such as multi-factor authentication, user management, and other security features.
The best approach will depend on the specific requirements and constraints of the organization and legacy application.
SAML and SSO
Security Assertion Markup Language (SAML) is a standard for exchanging authentication and authorization data between parties, such as an identity provider (IdP) and a service provider (SP).
When a user accesses a web page or application, the application redirects the user to the IdP for authentication. If the credentials are valid, the IdP creates a SAML assertion, an XML document containing information about the user’s identity and attributes, such as role assignments. The IdP sends the SAML assertion to the service or application.
The web page or application then uses the SAML assertion to authenticate and authorize access to the user’s resources.
SAML enables SSO by allowing the user to authenticate with a single identity provider and access multiple applications with one set of credentials.
Master SSO and authentication – Let Bluefletch be your guide!
Advanced Authentication Approaches
Outside of the traditional username and password; there are a variety of alternate authentication approaches for shared Enterprise Android devices.
Multi-Factor Authentication (MFA)
Two-Step Verification, or Multi-Factor Authentication (MFA), is a secure login method that requires two authentication factors.
MFA takes effect the first time a user signs into a device or application. Once they’ve entered their credentials, MFA prompts them to enter a “second factor” to verify their identity.
The second factor is commonly a randomly generated one-time code sent to their associated email or phone number. Once this unique code is entered, a user can access their account.
Two-Step verification’s second layer of security will soon be a standard in the industry as companies like Google and Microsoft are already urging users to adopt MFA.
Biometric Authetication
Biometric authentication is no longer limited to the reaches of science fiction. The fingerprint scanners and facial recognition devices that once only existed on the silver screen have become a reality.
Biometrics are helpful and precise data security tools to identify users, provide secure access, and protect devices and data. Biometrics utilize unique biological characteristics such as fingerprints, faces, and voices to identify users.
Popular examples of biometric authentication include:
Fingerprint Authentication
It uses a person’s fingerprint to create a digitally mapped value that can later be used to authenticate a user into a shared system or location. Fingerprint authentication has become a standard security feature in the consumer market since Apple popularized TouchID with the iPhone 5C in 2013.
This technology can also be used on various Android devices, and proves to be an efficient login method. Organizations will find that having users tap their fingerprint drastically reduces login time. By utilizing a biological feature, users can also reduce password fatigue. However, the adoption of fingerprint scanning may become unnecessary as facial recognition technology has become popular.
Facial Recognition (facerec)
Facerec has continued to gain momentum over the last few years as companies like Apple and Android are beginning to integrate forms of facial recognition into their company-owned devices.
Much like fingerprint authentication, facial recognition uses a mapped value of an individual’s facial features to create a unique passcode within a system. Facial recognition requires special hardware, such as a high-resolution front-facing camera that can detect and match facial features to the stored mapped value. This mapped value is stored securely within an organization’s database.
One primary concern of facial recognition is the extreme sensitivity of a user’s mapped value. As facial features are unique to each individual, the theft or exposure of a facial map could comprise someone’s identity. For these reasons, facial recognition has faced tremendous scrutiny and backlash, especially in light of the sheer number of organizational breaches that happen every year.
Voice Identification
Less common in consumer and enterprise use, voice ID uses the waveforms of a person’s voice to confirm their identity. This technology has begun to appear in the consumer market with devices like Amazon’s Alexa, which recognizes and remembers individual voices by tracing and storing vocal patterns.
Retina Scanning
As the name suggests, this form of authentication scans, maps, and stores a user’s retina for authentication. Retina scanning is quite a ways from reaching the enterprise market. As it stands now, technology is simply not refined enough to be helpful in the workplace. Not when more developed tech like facerec exists.
Biometrics on Shared Devices
Authenticators grant access to buildings, computer systems, databases, secure networks, devices, and so much more.
For shared device environments, biometric authentication dramatically increases the security an enterprise needs to maintain a safe digital workspace. Limiting access to company systems via unique physical attributes gives the workplace an extra sense of comfort.
The strength of biometric authentication lies in the unique nature of its requirements; utilizing biological information makes for a far more secure user experience than a traditional password. It is significantly more challenging to replicate a physical feature than to guess a set of characters and numbers. Biometric authentication limits potential threats at the source by redefining password standards.
However, this is no perfect system, as hackers can still exploit potential vulnerabilities. Just like the characters of a password, digital maps generated from a person’s fingerprint or face are susceptible to theft. This information is securely stored within a company’s database, but if a network is vulnerable, a hacker can exploit an opportunity to steal digital maps. Theft of a fingerprint scan has a far more detrimental effect on an end user. It is important to stay informed about the latest technologies and biometric information to keep your enterprise secure.
How do Biometrics Authenticate End-Users?
Biometric Authentication works similarly to password authentication, except that the end-user’s unique physical attributes replace digits and characters. A biometric authenticator uses the pattern or image of a physical trait, such as your fingerprint or face, to grant entry to shared systems, company databases, and physical buildings.
Everyone who needs access to a particular database or device is limited to their biological characteristics. A system will only permit a user who matches the biological information, such as a fingerprint, that is on file. Additionally, biometric authentication is possible across a fleet of workplace devices. A user can use multiple Android devices compatible with biometric authentication methods. That’s because biometric data is stored within an organization’s database, allowing authentication to occur across the enterprise.
For example, fingerprint scanners read the lines and grooves of a fingerprint to make a digital hash for storage. This is opposed to an exact picture or a replica of someone’s finger because of specific privacy laws that are set in place to protect individual privacy. The EU has a stringent regulation known as the General Data Protection Regulation (GDPR), which protects personal data by regulating how information is stored and used. Their official site states, “data includes genetic, biometric, and health data, as well as personal data revealing racial and ethnic origin, political opinions, religious or ideological convictions or trade union membership.”
Therefore, most systems utilizing biometric authentication typically leverage the digital mapping strategy instead of true copies to protect a user’s identity from hackers. The mapped value of the fingerprint is then stored securely in the device’s system, where it can not be accessed. The copy must be adequately secured since a compromised fingerprint could threaten a user’s safety and future security. When a person places their finger on a scanner, the system will trace out the lines of their fingerprint and match it to the digital map on file, eventually granting access once the fingerprint is recognized.
Matches do not have to be 100% accurate per the personal privacy regulations and the technology’s advanced understanding that biological attributes may become scarred or affected by natural causes.
This is an ideal scenario for enterprises that have workspaces with shared devices because authentication time is much quicker than entering a traditional password.
In a workplace utilizing biometric authentication, every person already has their password, making this form of authentication one of the most secure options for any enterprise that uses shared technology.
Biometric Security
An organization must maintain proper security protocols to protect digital mappings. Biometric data such as facial scans and fingerprint maps can compromise the safety and identity of the individual. Workplace systems storing this information need to understand the importance of protecting the identity of their employees.
Biometrics can be a valuable and welcomed authentication tool within the enterprise. Before adopting new technologies, check with your country, state, and local data privacy and protection laws.
Complexities with Authentication
Cleaning Up Data
Browser Data
In shared device environments, browser data can accumulate between shifts. Accessing insecure websites and dangerous web pages can threaten an organization. Retailers should implement browser wiping protocols to ensure data is cleared.
SSO allows organizations to customize how browser data is cleared. A continuous data wipe and blocking access to specific web pages keep shared environments safe.
Android Authentication and SSO Product Landscape
Various Launchers are available on the market to support Android devices. Some of the most notable solutions include but are not limited to:


Conclusion: The First Step is the Hardest
Shared Devices Need Security
Shared devices open up many opportunities for success in the retail environment. However, with success comes the burden of security risks and unique digital vulnerabilities. As the retail industry continues to trend toward shared device scenarios, the importance of mobile security has never been greater.
When company-owned devices are deployed in the field, organizations risk the safety of their employees, customers, and company data every day. Bad actors, thieves, and hackers have quicker access to sensitive data when systems patched into the company network are scattered about the store.
Retailers must understand that security is at the core of success in mobility, as without it, all the progress that can be made is irrelevant. Retail is one of the most breached industries, with cybersecurity threats coming from all angles. Organizations must remain vigilant by preparing appropriate security protocols and regularly monitoring device usage.
With a solid security foundation, a shared device fleet can run and continue to provide value to an organization.
Understand Security Posture and Tradeoff
No solution will align perfectly with the goals of an organization. Understanding the tradeoffs associated with implementing new technology like SSO takes time. The security posture of an organization measures the baseline for this success. Retailers must always maintain a strong understanding of their security protocols and the subsequent tradeoffs.
Start Small and Don't Boil the Ocean
Sometimes your eyes are bigger than your stomach, and the potential future benefits of a shared device fleet can overtake the reality of managing thousands of devices.
For organizations of all sizes, a sample size deployment and a shared device testing environment are the best places to start. Work out all the kinks in a controlled environment before scaling upwards to deploy a large fleet. Minor issues become mountainous if an organization deploys more devices than they’re prepared to handle.
Every workplace is unique, and each environment depends on many factors for maintaining a healthy security protocol. Test launches on small groups and pre-determined test sites allow for a pilot phase where an organization can learn how to control and manage a device fleet.
Giving space for mistakes creates a healthy, low-stakes opportunity for learning. Management teams, helpdesk professionals, and field employees can have time to evaluate, troubleshoot, and resolve potential issues. Additionally, surveying test groups and providing a chance for end-users to give feedback will be a valuable asset down the line.
Managing a device fleet is a tremendous amount of responsibility. Don’t let over-ambitious dreams of a better workplace destroy the potential of a well-thought-out plan. Organizations must treat their investment carefully and practice patience to grow the best outcomes.
Make it Easy for Your Teams
It takes a collection of teams across an organization to manage a device fleet successfully. These teams are comprised of individuals who will benefit and interact with devices the most. Organizations need to make it easy for these teams to adopt and grow with new technology before demanding results.
Not everyone will pick up on new technologies at the same pace. Make it easy for your teams by having demonstrations, Q&A sessions, and a streamlined set of instructions. Give employees time to adapt and learn SSO’s functionalities while learning about its security features’ importance.
By maintaining a safe and welcoming learning environment, employees will not only adapt to new technology quicker but also improve their day-to-day productivity. Efficiency comes in time, and so do all the benefits SSO comes with. By being prepared, organizations can find the best results.
Align to Long-Term Goals
A map is the best way to find your destination; the same can be said for deploying new technology. Before embarking on the journey toward a more efficient and secure retail environment, develop long-term goals. These goals are the wind that carries the sails of an organization and the horizon it’s headed toward.
To get the most out of a solution such as SSO, use existing long-term goals to evaluate and understand how SSO can help you. These goals should be the reason for beginning this journey; therefore, they should always be at the forefront.
BlueFletch is dedicated helping organizations looking to adopt or better understand the benefits of single sign-on and other enterprise mobile technologies. If you want to ask questions or hear more about what BlueFletch offers, don’t hesitate to contact info@bluefletch.com.