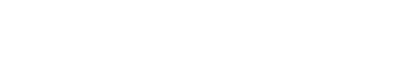To research this article, I browsed eBay for used Zebra devices and was surprised at how many are currently for sale. Did you know you can buy a used Zebra TC51 for $100 on eBay? It doesn’t come with a box or manual, and the seller states the device is reset to factory default. Closer inspection reveals the used handheld is the seller’s first item listed while their account was just days old. The seller claims they have “no need for it no [sic] more” and while I can’t say for sure, all signs lead me to believe this is a stolen device from one of the many enterprises with corporate-owned handhelds. As I continue scrolling, I find another device from a different account. This one also “does not include a charger, previously used in a pharmacy.”
Retailers spend anywhere between $300 and $2,000 on a single handheld device for use in the store. In the example above, the TC5X series from Zebra retails around $1,500 new. These high-ticket items are critical to an associate’s job and thus are constantly lifted and placed down during tasks. As a result, enterprise device theft has become more and more common. I can’t speak from experience, but thieves will look for any opportunity to get their hands on a high-value item, and a stray iPhone or unsupervised rack of CT40s will certainly catch their eye. This post will highlight security strategies to help prevent workforce device theft so that devices stay in your store – instead of for purchase on eBay.
Device Security in Retail Stores
Security is every IT organization’s top priority, but the primary focus is usually on the software, management tools, and OS of a device. The physical security of devices can often be an afterthought, but with hundreds or thousands of deployed devices in the wild, the risk profile is huge.
Over the years, I’ve done many store walks for retailers. While a majority practice secure methods to ensure devices don’t get stolen, there are plenty who could take additional steps to reduce company-owned device theft.
The first thing when beginning a store walk is to sign-in at the customer service desk. More times than not, there is at least one device lying on the desk within my reach. It’s not always reasonable to expect an associate to holster or pocket the device anytime it is not being used. This can be especially common for associates who work in big-box stores and need both their hands to operate equipment like ladders or forklifts.

Besides the in-use devices lying around a store, devices recharging must be kept in a secure area ideally near a manager’s office.
One store I visited had their rack of Zebra devices visible from the bathroom area without a locked door in between.
Enforcing the protection of devices at scale ultimately comes down to the human. Organizations must trust a user to protect the device at all times, but we know that people make mistakes or have lapses in judgment. Thieves are everywhere, and the sheer number of high-value handhelds in use at retailers creates a high likelihood of burglary.
So what can be done to counteract opportunities for company-owned device theft?

What are retailers doing to prevent theft?
- Strict check-in/check-out process
Some retailers require checking in with a manager for the assignment of a company-owned device, thus creating a paper trail. In one case, a retailer built a physical locker for the device and required a user to scan-in to unlock the cage. The BlueFletch Enterprise Launcher assists with device accountability by tying login to the device (rather than applications), creating a full audit trail for login and cradle events. - Device racks in secure locations
Usually a rack of charging devices will be kept inside or near a manager’s office. One client locked their devices inside a safe each evening, but this presented its own separate problems for connectivity. While we wouldn’t recommend this approach, it highlights the lengths retailers are willing to go to deter device theft.
What are OEMs doing to bolster device security?
- Proprietary USB cables
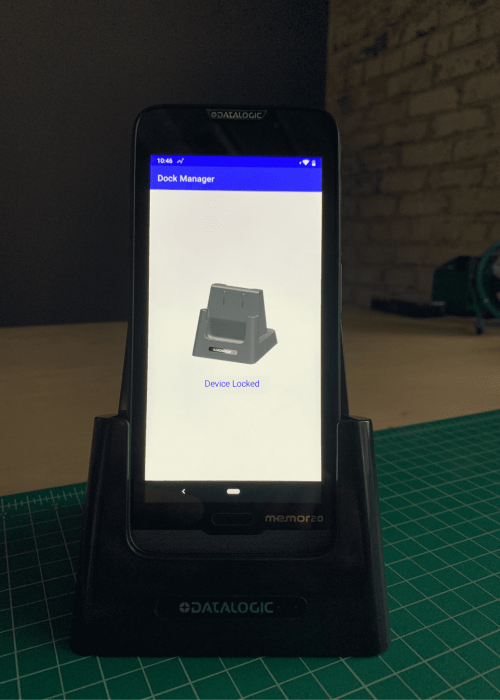
Many of the rugged Android devices do not include a USB-C or micro-USB port for data transfer. The cables are specific to the device and have an additional cost. Making it more difficult to pull data from a device via USB (which should be disabled from your EMM anyway) prevents any data that has been synced locally on the device from being compromised. - Locking cradles
Shown at the National Retail Federation (NRF) in 2020, one OEM is adding a physical lock inside of the charging cradle. In order for a device to be removed from the dock, they must check-out the device via login or some type of badging. BlueFletch is looking to potentially integrate our Enterprise Launcher login flow to trigger the unlock of the cradle after successful login. - Batteries with separate beacons that can’t be powered off
Relying on a device to send an alert when it leaves a space can be great, but what happens if the battery is removed before the device is taken out of the retail location? OEMs are looking into adding a beacon within the battery that can’t be powered down and will transit their signal until the battery is completely depleted.
What is Google doing to help?
- Zero-Touch enrollment
While this isn’t technically a physical security measure, ZTE does impact future use of hardware after a reset. With the new Android Enterprise ZTE process, a carrier or VAR designates a device as owned by an organization and belonging to an EMM. This bond can only be broken by the carrier or VAR, so when a stolen device is factory reset it will forever attempt to enroll into the organization’s EMM. This renders the device unusable and only value for individual parts (like batteries or screens).
- StrongBox Keymaster
Starting with Android Pie, devices can have a StrongBox Keymaster module containing:
-It’s own CPU
-Secure storage
-A true random-number generator
-Additional mechanisms to resist package tampering and unauthorized
sideloading of appsIn the future, this can be used to harden security on devices by creating lockdown keys unable to be hacked or altered.
Ways we have helped retailers reduce device shrink
At BlueFletch, we have helped a lot of retailers migrate to modern dedicated Android devices. The subject of how to deal with company-owned device theft has come up numerous times, and it’s something we’ve had to help clients build security protocols around. The following are the more common ways that we have helped reduce device theft:
Prevent devices from sitting around
We have all set our keys down somewhere and forgotten about them. The same thing happens with mobile devices. Unfortunately, sometimes the next person to pick them up is not one of your employees. We incorporated a “device finder” feature into our EMS Support Agent to help employees located misplaced devices. It also has battery functionality that will trigger an audible notification if a device is not moving or falls below a certain battery level.
Set devices to lost luggage mode upon being disconnected from networks
We have built functionality that allows you to trigger the device in a lost screen mode for situations where the device is no longer able to connect to the network.
The message can be customized to indicate something to the effect of “This device belongs to Retailer XYZ. Unauthorized usage of this device may be illegal. If found, please return this device to your closest XYZ location.”
Create a sense of accountability among employees
With our Enterprise Launcher, Store Managers are able to know who had a device last and if it was returned to a cradle. Having visibility into this information helps drive device accountability among employees. One of our clients has gone as far as reprimanding employees if they don’t return devices correctly at the end of their shift. Across our clients, companies that create a sense of employee accountability have seen less company-owned device theft.
In addition to the above, we have helped build more complex security functionality that we are not allowed to discuss publicly. If you have a custom solution you are looking to implement, or if you have other questions about leveraging any of our EMS tools, we would love to hear your feedback. You can reach out to us at info@bluefletch.com.