The Elephant Zebra in the Room
Enterprise mobility’s elephant in the room is that Android security patches are rarely applied to the corporate-owned mobile fleet. The mobile operating system is a proven vehicle for attack via vulnerabilities in the OS, and yet companies struggle to apply patches in a timely manner.
Google proactively (and sometimes reactively) releases monthly patches for Android via the Security Bulletin. The same patches are provided to device manufacturers, like Zebra, for inclusion in their custom Android OSs. Those builds, called LifeGuard™ by Zebra, provide security and support beyond the standard 3-year support window for Android. Extending support with security patches extends the life of rugged devices in the enterprise and lowers the cost of ownership. Learn how to Upgrade your Zebra Symbol Android Device here!
Are you scheduling OS patches into your mobility release schedule? If a critical patch is required (e.g. Spectre), how quickly can your organization test, schedule and deploy across hundreds–or thousands–of corporate devices?
Full Upgrades are Not That Simple
Full Android OS Upgrades (e.g. from Nougat to Oreo) are rare for enterprise rugged devices. The main reasons why we see companies avoiding full updates include:
- Cutting-edge features are unnecessary – Cutting-edge features are seldom required for common business usage. The bulk of improvements for Android devices are focused on new consumer features.
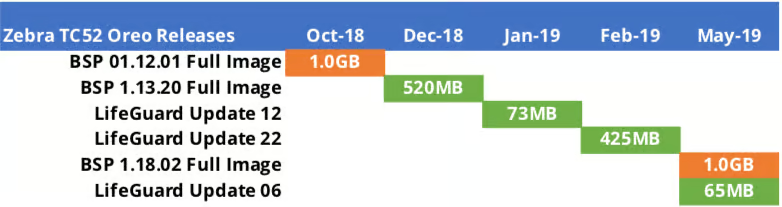
- File size impact on Infrastructure – Large OS files are difficult to download over highly-utilized end user environments. Even worse, downloading large files can bring devices to a halt in the middle of employees performing key tasks.
- App Compatibility – Applications written by internal development teams must be rebuild and compiled for the new Android OS version.
- Change is Chance – Unnecessary changes can cause instability in environments. Making changes in infrastructure can have unforeseen impacts on mission critical Line of Business applications.
Due to the above reasons, most organizations we have worked with do not have a proactive strategy for performing standard OS upgrades and typically avoid regular patch upgrades to their business-critical devices to avoid the headache. As a result, we built an OS Upgrade Tool for Zebra that ensures Android OS and security patches complete on the first try, without failure….and without the headache.
Historically, defense in-depth security measures have helped to mitigate this lack of patching, but as more critical functionality is pushed to these devices, security must be treated as a priority. This is especially true for devices that are connecting to wireless in stores, warehouses, or field locations (see the recent WPA2 Android KRACK vulnerabilities).
Organizations need to begin planning and budgeting for regularly scheduled patching of their devices. Each patch might not be applicable for your fleet, but getting in a regular cadence will help give you the confidence to quickly take action if need be. An additional benefit we have found is that a device on the currently patch level will typically get faster issue turnaround from the Zebra support team.
Tactical Approach for Smoother Upgrades
In the past, I’ve experienced all the pains that go along with OS upgrades and updates that often scare teams away. However, going through that experience –even just once– with your mobility team will provide the knowledge, framework, and process for repeating the exercise on a regular basis.
Having an answer for these questions will guide what tasks must be completed in preparation for a pilot:
- Landing Files: Where will the upgrade .zip be hosted? Will it be downloaded from your EMM/MDM? How will the host handle hundreds of requests during implementation? Can you leverage existing store infrastructure to enable devices to pull from local servers?
- Controlling the flow and execution: Can you “hydrate” (download required files) devices during a period of limited network utilization? Are you able to ensure the device is cradled and has at least 30% of battery life, as required by Zebra?
- Ensuring persistence/recoverability: Can you ensure that the device will remain secure and locked down after an update? For OS upgrades, will all apps persist and reinstall? Do network settings and security certs remain?
- Testing end-to-end on many devices: How will the process behave when scaling efficiently up to 30+ devices on a single network? How will problem or non-compliant devices behave?
- Regression Testing for apps and device functionality: Are app teams prepared to run through test cases against new OS version and provide sign-off? How quickly can you perform a regression test of the SOE (Standard Operating Environment) after the foundation just shifted to ensure functions like Datawedge operate as desired?
- What are the constraints of your MDM? Are you able to time-box deployments to not interfere with business operations? Can you configure the download location of OS Upgrade .zip, or must it be hosted in the MDM’s server?
- Reporting state of devices: What is the baseline of a known good state device: free space, battery health, etc.? Can you query to find the number of “healthy” devices and estimate success rates? (BlueFletch Support Analytics can answer these questions and more via dashboards or ad hoc queries. For more info please visit this link).

- Reporting state of devices: What is the baseline of a known good state device: free space, battery health, etc.? Can you query to find the number of “healthy” devices and estimate success rates? (BlueFletch Support Analytics can answer these questions and more via dashboards or ad hoc queries. For more info please visit this link).
- Understanding your MDM: What are the constraints of your MDM? Are you able to time-box deployments to not interfere with business operations? Can you configure the download location of OS Upgrade .zip, or must it be hosted in the MDM’s server(s)?
Keep it Simple
Simplify Android updates by embracing them. Ensure apps can be quickly regression tested after a change to the Operating System. Get the update into a pilot site and allow a week or two of heavy usage. Build the process so when the next KRACK security patch is released, devices are protected within weeks — not months. Always keep an eye on the horizon as it is easy to get behind; incremental updates are much more reliable than large jumps in Android versions.
If you are still struggling, BlueFletch created a custom OS Update application from field experience to increase success rates via validations and checkpoints. We’ve also included helpful features such as smart downloading from multiple locations, power conditions, external logging and more. Contact info@bluefletch.com if you’d like to learn more.
Editors note: This post was originally published in August 2018 and has been completely revamped and updated for accuracy and comprehensiveness.