Employee login can become a headache for IT teams at growing companies. When employees have to juggle dozens of usernames and passwords to access all their business apps and accounts, productivity takes a hit. Help desk tickets for password resets pile up. Security risks increase as employees reuse passwords or use weak credentials.
Implementing a single sign on (SSO) solution at the corporate level can provide relief. With corporate SSO, employees can access all their accounts and applications with one set of login credentials. This simplifies the login process for employees while allowing IT to better manage user access.
Corporate SSO also provides security benefits. With SSO, IT has visibility into all employee application access through one identity management system. Strong password policies can be enforced across all apps. Authentication methods like multi-factor authentication (MFA) can be implemented at the SSO level as well.
Let’s explore the benefits of corporate SSO and what to look for in an enterprise SSO solution.
How Does Corporate Single Sign On Work?
With single sign on, users log in once with a single ID and password to a central portal. This could be hosted on-premises or through a cloud SSO provider.
Once logged in, users can seamlessly access all their web and SaaS applications without re-entering credentials. SSO software integrates with each application through standards like SAML and OpenID Connect.
When users log in to the SSO portal, it passes their credentials to the integrated apps behind the scenes. This allows them direct access without any secondary login screen.

Benefits of Corporate SSO
Streamlining login delivers several advantages:
- Improves productivity – Employees aren’t bogged down entering credentials repeatedly. Studies show workers can save 8-15 minutes per day with SSO.
- Enhances security – IT can enforce strong password policies and MFA across all apps. Employees won’t be tempted to use weak passwords.
- Reduces IT tickets – Fewer login issues means fewer password reset calls to the help desk.
- Centralizes access management – Admins manage user accounts and permissions in one place instead of individually in each app.
- Enables self-service – Users can request application access through self-service workflows rather than IT acting as gatekeeper.
- Works with cloud apps – SSO integrates both on-prem and cloud applications into one access portal.
Top SSO Solutions for Enterprises
Many SSO platforms exist for handling identity management at an enterprise scale. Leading options include:
- Microsoft Azure AD – Cloud-based identity and access management solution to integrate Microsoft apps and third-party SaaS tools.
- Okta – Popular cloud identity platform with pre-built integrations for thousands of apps.
- JumpCloud – Agent-based SSO provider focused on centralizing directory services across devices, apps, files, and networks.
- Centrify – On-prem and cloud SSO focused on integrating Active Directory with cloud apps and mobile devices.
- OneLogin – Compliance-centric cloud identity platform with advanced access management capabilities.
Evaluate providers based on your environment and specific use cases. For most, a cloud platform like Okta or Azure AD simplifies deployment. On-prem options like Centrify allow tighter Active Directory integration.
Key Considerations for Corporate SSO Procurement
Here are some key aspects to consider when evaluating and implementing an enterprise SSO solution:
- User provisioning – Does it offer automated user setup and deprovisioning?
- Pre-built app integrations – How many apps come pre-configured to simplify connections?
- Access policy engine – Can you implement contextual or step-up authentication policies?
- Device and mobility management – What options exist for mobile SSO and device management?
- Admin user controls – Does it provide delegation of duties and separation of concerns?
- Security standards support – Does it enable standards like SAML, OIDC, OAuth 2.0?
- Deployment flexibility – Can you start in the cloud and move on-prem later if needed?
- Reporting and analytics – Does it provide audit logs and usage analytics?
By approaching SSO implementation with a business-driven lens and comparing vendors across these criteria, you can select the right solution for your organization’s identity management needs.
Understanding the Technical Side of SSO Authentication Flows
While SSO aims to create a seamless login experience for end users, behind the scenes it relies on some technical protocols to securely pass identity credentials between applications. Here is a quick overview of how SSO authentication works:
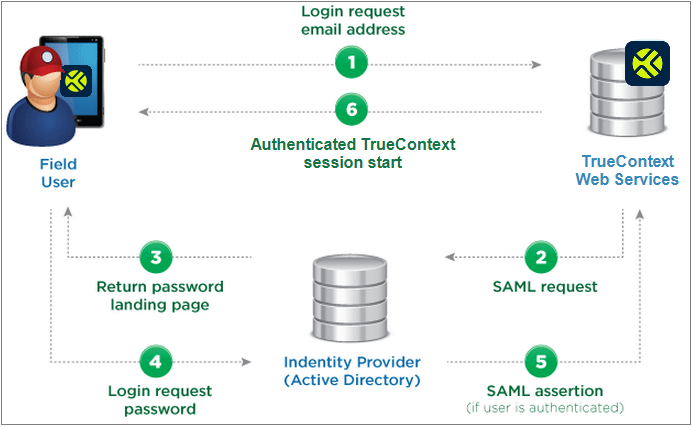
When a user attempts to access an application, the application sends a request via a protocol like SAML or OAuth to the SSO identity provider to authenticate the user.
If the user has an active SSO session, the identity provider immediately returns an authentication token to the application granting access.
If there is no active session, the user will be redirected to the SSO login page to enter their credentials. This is where any additional authentication factors like MFA would also come into play.
Once authenticated, the identity provider issues a token containing the user’s verified identity to send back to the application. The application validates the token signature to confirm it came from a trusted source.
The user is then able to access the application without re-entering credentials until the SSO session expires. This token passing happens seamlessly in the background at each application.
On-Premises SSO Deployment Options
While cloud-based SSO providers simplify deployment, some organizations may prefer an on-premises SSO solution. Reasons can include:
- Tighter integration with existing on-prem identity stores like Active Directory
- Ability to keep identity infrastructure fully within your control
- Compliance requirements to keep authentication on-network
- Large existing IT infrastructure investments
On-prem SSO integrates with directory services like AD via standards like SAML or LDAP. This allows seamless pass-through of internal user identities to SSO.
Leading options like RSA SecurID and ForgeRock work for both cloud app SSO and internal web apps. This provides one unified SSO solution covering all use cases.
Deployment is more hands-on than cloud SSO setup but gives companies full control over their identity infrastructure. On-prem SSO can also be used alongside cloud-based SSO solutions.
SSO Security Risks and How to Mitigate Them
While SSO improves security in many ways, it can also introduce potential risks:
- Single point of failure – Breach of the SSO provider could expose all applications. Mitigate by compartmentalizing access and using MFA.
- Overprivileged access – Users have access to all apps allowed by SSO policy. Limit assigned apps based on user role.
- Weak primary credentials – Main SSO login is key vulnerability. Enforce strong password policies and multiple factors.
- Limited application security – SSO might bypass app-level security. Configure app logins to use SSO for authentication but retain app access controls.
- Account hijacking – Takeover of user’s SSO account grants access to all apps. Use risk-based authentication via device trust, location, etc.
With proper SSO architecture and access policies, organizations can reduce these risks and leverage SSO to improve overall security posture.
Frequently Asked Questions (FAQs) About Corporate SSO
SSO specifically refers to streamlining login through a single set of credentials. IAM (identity and access management) is the overall framework for managing user identities, while Active Directory is Microsoft’s directory service. SSO software integrates with IAM and AD to enable centralized login.
Properly implemented SSO improves security by centralizing access control and enabling stronger, consistent authentication policies across applications. Leading SSO platforms incorporate robust security protections.
Quality SSO solutions provide pre-built integrations for thousands of popular SaaS apps. They also support standards like SAML and OIDC to connect virtually any application, whether cloud, on-premises, mobile, or legacy.
Yes, SSO platforms provide options for securely granting external user access such as customers, partners, and contractors. This includes capabilities like external identity providers, guest user management, and selective application access.
Modern SSO platforms are designed for quick and simple rollout. Cloud-based systems like Okta allow companies to be up and running in days or weeks. Onboarding users and apps is highly automated after initial configuration.
Streamline Login and Access for Your Organization
Corporate single sign simplifies login for employees while giving IT teams improved control and security over access. Leading enterprise SSO solutions make it easy to get started and deliver tangible benefits from day one.
To determine how SSO can benefit your organization, reach out for a consultation. We can assess your existing apps, identity management, and use cases to map out the right solution. Whether cloud, on-prem, or hybrid, SSO can transform how your company manages access for the modern digital workforce.