What is Ransomware?
In a recent interview on the a16z Podcast alongside fellow cybersecurity expert Tom Hofmann, Joel de la Garza stated that ransomware is the fastest-growing threat to cybersecurity in the world. Criminal operations capture vital networks and set global corporations back tens of millions of dollars just to retrieve their own data. Ransomware has easily become one of the most lethal forms of digital crime, but what is it?

Ransomware is a form of cybercrime that uses malware technology to take data hostage in exchange for cryptocurrency such as Bitcoin. Stolen information is locked through advanced encryption techniques that leave businesses desperate for a decryption key. Criminals force organizations to pay large sums of money or risk endangering their company and employees. As the rate of ransomware continues to climb with the rise in digital networks, it is more important than ever to keep yourself informed and protected.
How does it work?
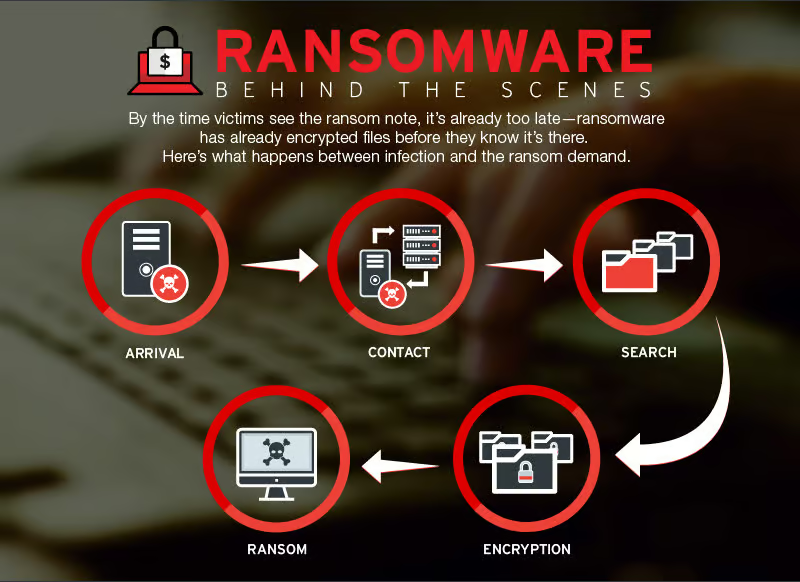
These criminal infrastructures usually run as a “hack-for-profit” and use teams of computer experts to run the operation. Hackers take advantage of weak cybersecurity by deploying waves of malware to gain access to valuable data within a company’s network. Utilizing tools such as Cobalt Strike allows for malware to make continuous attempts to break into ports within internal and external networks. This process is usually executed through phishing, email spamming, or password guessing.
Tom Hofmann stated that most companies are more concerned about protecting their external networks, leaving internal ports exposed. This little mistake is what leaves certain networks unpatched and available to be hacked. Once breached, the malware heavily encrypts the system, locking both the hardware and software. Anything taken hostage is useless and inaccessible until the ransom money is paid in full. Sometimes hackers leave victims with a timer or an ultimatum as a way to scare companies into dishing out their ransom. Once a victim has paid up, hackers will automatically release an encryption key so the business can begin to gain their data back. Fully recovering all encrypted data may take weeks, but criminal organizations are very wary of their reputation and almost always deliver on their promises.
Who is being targeted?
A recent statistic by Statista shows that in 2020 there were around 304 Million incidents worldwide, 62% more than in 2019. Essentially any company, organization, or corporation that uses technology to store its data is vulnerable to be attacked. For instance, hospitals have recently fallen victim to ransomware, even leading to the death of a patient. Cybercriminal infrastructures will target anyone they can squeeze money out of, even if it means destroying lives. These crimes are not exclusive to businesses though, individual people can be targeted as well.
What kind of data is usually taken, hostage?
As we move further into the digital age, almost every company has digitally stored their valuable information such as:
- Employee bank information
- Social security numbers
- Home addresses
- Company bank accounts
- Insurance policies
Criminals will collect any data that is valuable to their victims so having access to insurance policies and bank records is huge. They can conclude ransom amounts based on what a company can afford or cover with insurance. Therefore, locking a victim into a negotiation they can’t win. Threatening to expose sensitive employee information is another way that these criminals entrap organizations into a dilemma.
Why should my enterprise get protection?
You need protection If digital databases secure your company’s vital information.
Here’s why:
- Company databases
- Your company’s data may be essential to keeping your business afloat; losing it could mean professional ruin.
- If your company can not afford to pay a ransom, the criminals may do as they please with your network, ultimately rendering your company helpless.
- Financial Security
- The average ransom rose to multi-millions, so being targeted can destroy your precious data as well as your financial standing.
- Employee Information
- Ransomware hackers will likely threaten to expose private information about employees. This includes financial information, social security numbers, addresses, etc.
- Keeping your people safe is number one!
- Clients
- A client’s information may be leaked. This can threaten your professional reputation and potentially ruin a client’s life as well.
- Yourself
- In some cases, handing over money to a crime syndicate can land you in legal trouble or even jail time. Because the world of digital crime is still new, the laws have not been developed enough to protect every victim.

How do I stay protected?
Thankfully there are many ways to ensure your company’s protection from cyber attacks. However, Due to the ambiguous nature of the online world, there is no one “silver bullet” to stopping ransomware. Garza and Tom mention that “good IT hygiene” is a top priority, so here are a few ways to stay safe as listed in their article 16 Steps to Securing Your Data (and Life):
- Frequent software updates & patches
- Always ensure your network and software are up to date.
- Two Factor Authentication
- Ensure all employees have activated TFA to stay secure.
- Trust and be aware of what you install
- Hackers can enter malware through corrupted links and emails. Make sure to research and verify anything you install.
- Password Managers
- They help organize and create secure passwords for you and your employees.
Conclusion
In a world moving toward a digital future, it is time to take the steps to protect you and everything you love. Ransomware is an extremely dangerous crime that is beginning to infect millions of businesses across the globe. Start being safer by adopting better IT hygiene and staying up to date on the latest tech news! Being conscious of the dangers within cyberspace could save your enterprise from a potential breach.
